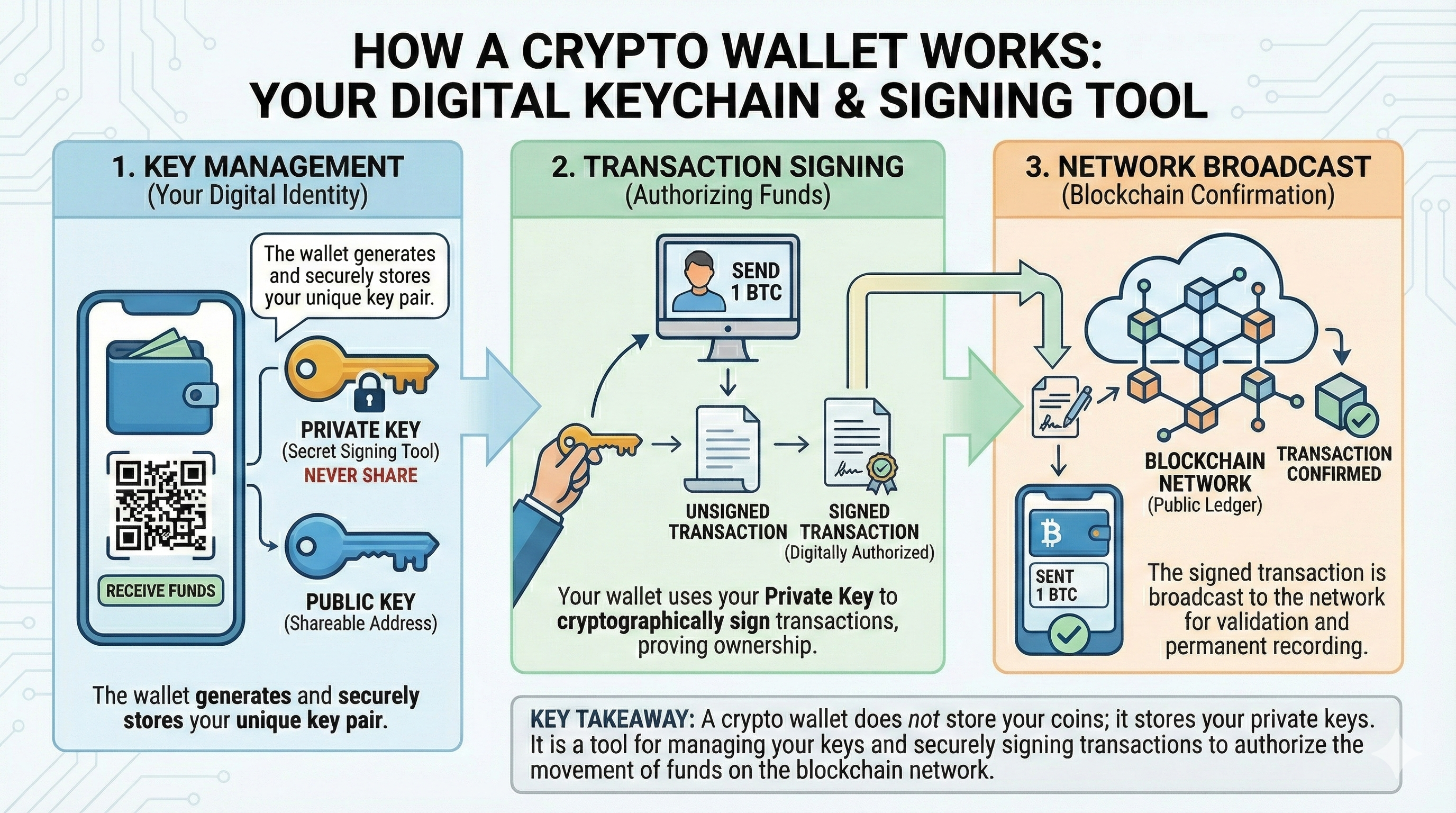
A hardware wallet is a discrete device that generates and stores the wallet’s private keys offline.
When you need to sign a transaction, the software sends the unsigned transaction data to the device. The user signs the transaction using the hardware wallet’s offline keys, and the device sends back only the completed signature. This process ensures that even if the computer being used is infested with malware, the private keys remain protected.
The hardware wallet serves as the primary firewall between your wealth and online threats. Like any crypto wallet , a hardware wallet does not actually “store” your coins; those live on the blockchain . Instead, the device stores the private keys that control your assets on the blockchain. Using a hardware wallet provides better security for the private keys, and by extension, the associated blockchain assets.
The Security of Isolation #
Computers, tablets, smartphones, and even apps and operating systems can be compromised or contain bugs that may put keys stored on an internet-connected device at risk. Hardware wallets address this risk in several ways.
- Private keys are generated on-device. At setup, the hardware wallet generates your seed phrase using a True Random Number Generator (TRNG). This occurs on the device itself. The seed and private keys remain isolated from your computer.
- Physical verification is required. To sign a transaction, the user must perform a physical action with the device. For traditional wallets, this is a button press; for card-style wallets, it is the physical act of “tapping” the card against an NFC-enabled phone. This ensures no transaction can be broadcast without a manual, physical trigger.
- Secure Element (SE) Chip. Many modern hardware wallets use a Secure Element (SE) chip to store the keys, the same tech found in smartphones, passports, and credit cards. These chips are tamper-resistant, and many can automatically “self-destruct” if tampering is detected.
Why It Matters #
Although hardware wallets typically use companion apps, the reliance on software shifts further toward well-established hardware security, including SE chips.
1. Reduced Risk: Many crypto thefts center on remote hacking, including hacks against wallet apps, but keeping the private keys offline counters many online risks. Most hardware wallets also use a PIN (Personal Identification Number) that serves as a local password.
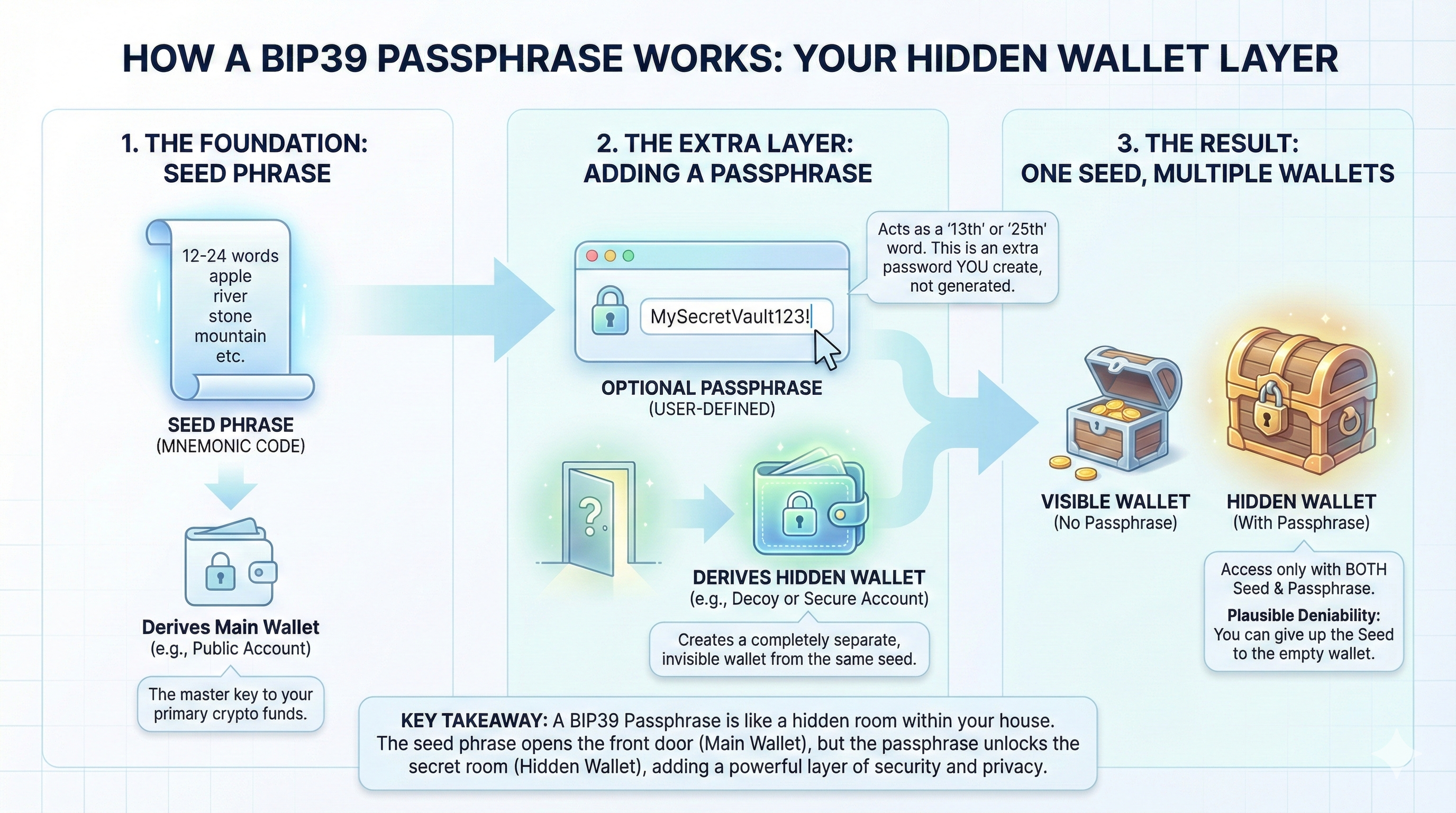
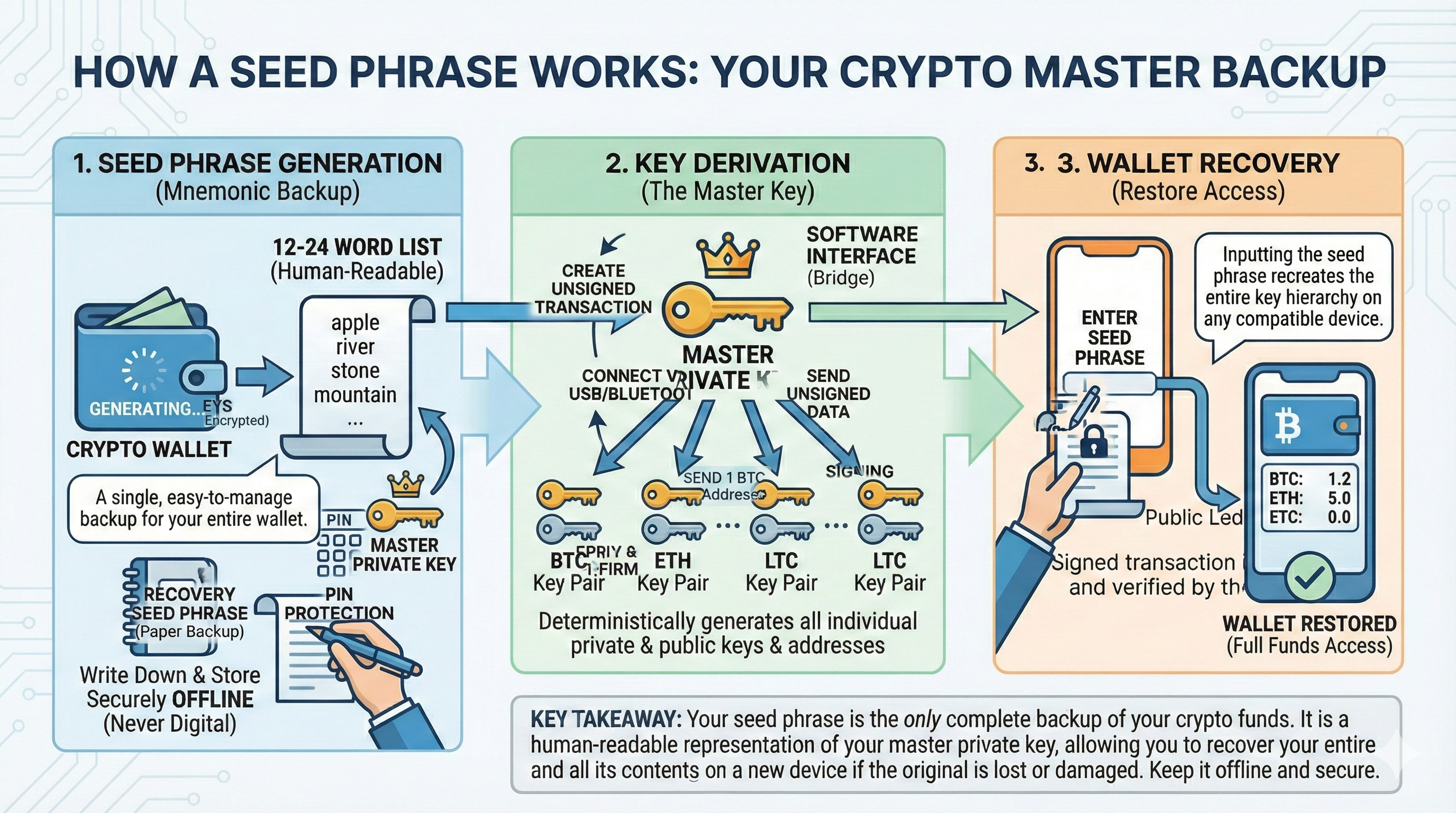
2. Hardened Recovery via Seed Phrases: Hardware wallets follow industry standards (like BIP39), allowing you to back up your master key onto physical media like paper or steel. This creates a redundant system in which the hardware can be destroyed, lost, or upgraded without risk to the underlying assets. Restore the seed to any compatible wallet.
3. Verification of Intent: Software wallets can be manipulated to show you one address while sending your funds to another. A hardware wallet provides a “Trusted Display.” By checking the transaction details on the physical device’s screen before clicking the button, you ensure that the transaction you are signing is exactly the one you intended.
Choosing the Right Device #
Not all hardware wallets are created equal. Some prioritize ease of use via Bluetooth, while others prioritize “maximized sovereignty” through completely air-gapped communication (using QR codes or microSD cards). The choice often depends on your specific threat model and how often you need to move your funds.
The Bottom Line #
A hardware wallet acts as an offline signing tool that keeps your private keys isolated from the risks of the digital world. While the device is a powerful tool for self-custody, it is only as secure as the physical backup of the seed phrase it generates.